Dimitrij Klesev & Andreas Zeissner
Enhancing Workload Security in Kubernetes
#1about 3 minutes
Understanding the Kubernetes securityContext for workloads
The securityContext field in a pod specification allows you to define privilege and access control settings for a pod or container.
#2about 4 minutes
Restricting kernel system calls with seccomp profiles
Seccomp profiles enhance security by allowing you to explicitly define which kernel system calls a containerized workload is permitted to make.
#3about 4 minutes
Hardening file system access with AppArmor profiles
AppArmor provides mandatory access control by defining profiles that restrict application capabilities like file reads, writes, and network access.
#4about 6 minutes
Implementing fine-grained control with SELinux contexts
SELinux uses a labeling system to enforce mandatory access control policies, providing granular control over process and object interactions.
#5about 2 minutes
Automating security with the Security Profiles Operator
The Security Profiles Operator simplifies the management and distribution of seccomp, AppArmor, and SELinux profiles across all nodes in a Kubernetes cluster.
#6about 5 minutes
Demo of blocking an in-memory execution attack
A live demonstration shows how a seccomp profile can block the `memfd_create` system call to prevent a fileless malware execution attack.
#7about 3 minutes
Demo of managing seccomp with the operator
This demo illustrates how the Security Profiles Operator uses a `ProfileBinding` to automatically apply a seccomp profile to workloads based on their image.
#8about 8 minutes
Demo of troubleshooting SELinux permissions
A practical demonstration shows how SELinux denies access by default and how to use audit logs and tools like `audit2allow` to diagnose and create new policies.
#9about 8 minutes
Q&A on AppArmor, fileless attacks, and eBPF
The speakers answer audience questions about applying AppArmor profiles, the nature of fileless malware, discovering system calls, and the role of eBPF.
Related jobs
Jobs that call for the skills explored in this talk.
Technoly GmbH
Berlin, Germany
€50-60K
Intermediate
Network Security
Security Architecture
+2
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
Matching moments

01:06 MIN
Malware campaigns, cloud latency, and government IT theft
Fake or News: Self-Driving Cars on Subscription, Crypto Attacks Rising and Working While You Sleep - Théodore Lefèvre

01:15 MIN
Crypto crime, EU regulation, and working while you sleep
Fake or News: Self-Driving Cars on Subscription, Crypto Attacks Rising and Working While You Sleep - Théodore Lefèvre
05:01 MIN
Comparing the security models of browsers and native apps
Developer Time Is Valuable - Use the Right Tools - Kilian Valkhof

03:16 MIN
Improving the developer feedback loop with specialized tools
Developer Time Is Valuable - Use the Right Tools - Kilian Valkhof

06:33 MIN
The security challenges of building AI browser agents
AI in the Open and in Browsers - Tarek Ziadé

01:32 MIN
Organizing a developer conference for 15,000 attendees
Cat Herding with Lions and Tigers - Christian Heilmann
09:38 MIN
Technical challenges of shipping a cross-platform browser
Developer Time Is Valuable - Use the Right Tools - Kilian Valkhof

05:55 MIN
The security risks of AI-generated code and slopsquatting
Slopquatting, API Keys, Fun with Fonts, Recruiters vs AI and more - The Best of LIVE 2025 - Part 2
Featured Partners
Related Videos
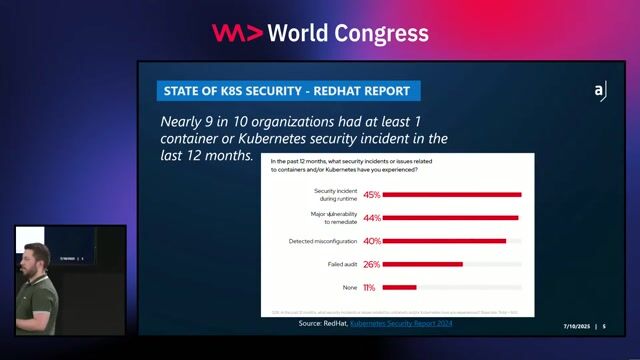 23:08
23:08Kubernetes Security Best Practices
Rico Komenda
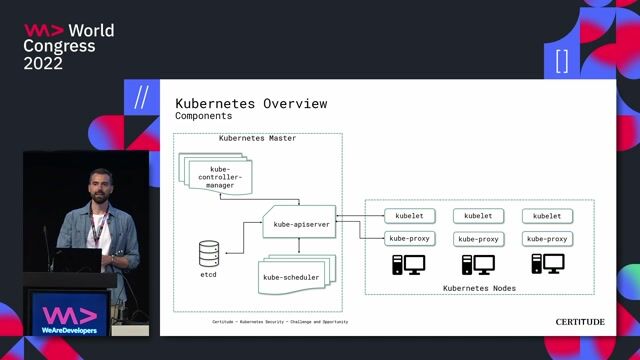 42:45
42:45Kubernetes Security - Challenge and Opportunity
Marc Nimmerrichter
 46:36
46:36Hacking Kubernetes: Live Demo Marathon
Andrew Martin
 58:52
58:52Securing secrets in the GitOps Era
Davide Imola
 58:57
58:57Securing Secrets in the GitOps era
Alex Soto
 33:20
33:20DevSecOps: Security in DevOps
Aarno Aukia
 39:20
39:20Developing locally with Kubernetes - a Guide and Best Practices
Dan Erez
 57:09
57:095 steps for running a Kubernetes environment at scale
Stijn Polfliet
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.





CompuSafe Data Systems AG
Berlin, Germany
Remote
Senior
Bash
Linux
Scrum
DevOps
+4

inovex GmbH
Karlsruhe, Germany
€60-75K
Azure
Kubernetes
Google Cloud Platform
Amazon Web Services (AWS)

Rocken AG
Bern, Switzerland
Remote
Linux
DevOps
Kubernetes
Microservices

QCG Computer GmbH
Eschweiler, Germany
Intermediate
Azure
DevOps
Puppet
Ansible
Terraform
+3

Plexus Tech
Municipality of Madrid, Spain
Go
DevOps
Python
Kubernetes
Amazon Web Services (AWS)