Mathias Tausig
Turning Container security up to 11 with Capabilities
#1about 8 minutes
Demonstrating a man-in-the-middle attack between containers
A proof-of-concept shows how a malicious container can sniff unencrypted traffic between other containers running on the same host.
#2about 5 minutes
Introducing Linux capabilities for granular privilege control
Traditional Unix permissions are an all-or-nothing model, whereas Linux capabilities split root privileges into distinct units for finer control.
#3about 4 minutes
Differentiating between file and process capabilities
Capabilities can be set on files to elevate privileges for specific binaries or on processes to reduce them, with the latter being key for containers.
#4about 3 minutes
Managing default container capabilities in Docker
Docker grants a default set of powerful capabilities to containers, which can be restricted using `cap-drop` and `cap-add` flags.
#5about 4 minutes
Securing deployments by dropping unnecessary capabilities
By dropping all capabilities and only adding back the essential ones, the man-in-the-middle attack is successfully prevented in both Docker and Kubernetes.
#6about 3 minutes
Using capabilities as a defense-in-depth measure
Limiting capabilities does not prevent an initial exploit but significantly reduces the potential impact and blast radius of a compromised container.
Related jobs
Jobs that call for the skills explored in this talk.
VECTOR Informatik
Stuttgart, Germany
Senior
Kubernetes
Terraform
+1
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
Power Plus Communications
Mannheim, Germany
Intermediate
Senior
Docker
Kubernetes
+2
Matching moments

01:06 MIN
Malware campaigns, cloud latency, and government IT theft
Fake or News: Self-Driving Cars on Subscription, Crypto Attacks Rising and Working While You Sleep - Théodore Lefèvre
07:39 MIN
Prompt injection as an unsolved AI security problem
AI in the Open and in Browsers - Tarek Ziadé
05:01 MIN
Comparing the security models of browsers and native apps
Developer Time Is Valuable - Use the Right Tools - Kilian Valkhof
09:38 MIN
Technical challenges of shipping a cross-platform browser
Developer Time Is Valuable - Use the Right Tools - Kilian Valkhof

06:33 MIN
The security challenges of building AI browser agents
AI in the Open and in Browsers - Tarek Ziadé

01:15 MIN
Crypto crime, EU regulation, and working while you sleep
Fake or News: Self-Driving Cars on Subscription, Crypto Attacks Rising and Working While You Sleep - Théodore Lefèvre
09:00 MIN
Navigating the growing complexity of modern CSS
WeAreDevelopers LIVE – You Don’t Need JavaScript, Modern CSS and More

02:33 MIN
Why you might not need JavaScript for everything
WeAreDevelopers LIVE – You Don’t Need JavaScript, Modern CSS and More
Featured Partners
Related Videos
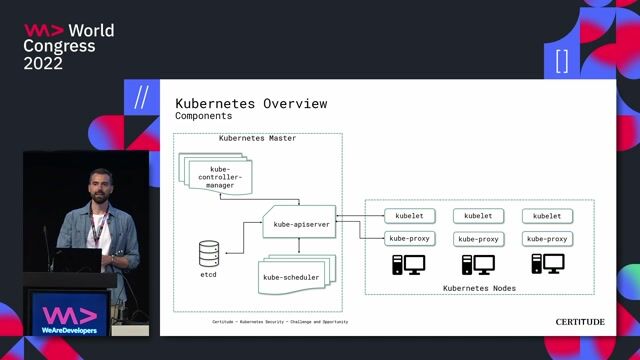 42:45
42:45Kubernetes Security - Challenge and Opportunity
Marc Nimmerrichter
 46:36
46:36Hacking Kubernetes: Live Demo Marathon
Andrew Martin
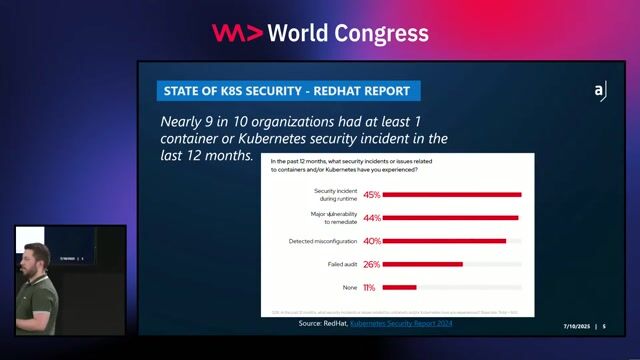 23:08
23:08Kubernetes Security Best Practices
Rico Komenda
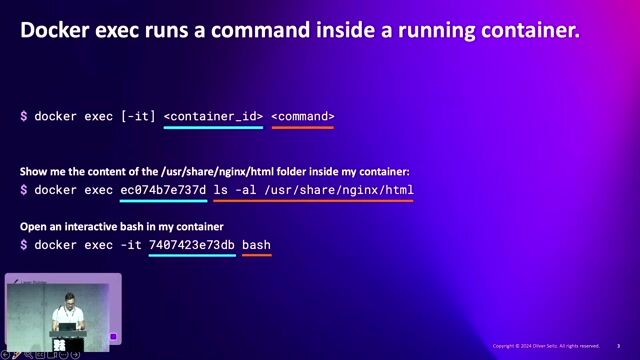 29:16
29:16Docker exec without Docker
Oliver Seitz
 24:47
24:47Supply Chain Security and the Real World: Lessons From Incidents
Adrian Mouat
 21:49
21:49A Hitchhikers Guide to Container Security - Automotive Edition 2024
Reinhard Kugler
 50:09
50:09Compose the Future: Building Agentic Applications, Made Simple with Docker
Mark Cavage, Tushar Jain, Jim Clark & Yunong Xiao
 28:41
28:41101 Typical Security Pitfalls
Alexander Pirker
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Raiffeisen Schweiz
Zürich, Switzerland
CHF110-130K
Bash
Azure
DevOps
Python
+6

Softwarezentrum Böblingen/Sindelfingen e.V.
Böblingen, Germany
Remote
Intermediate
GIT
Bash
Azure
Linux
+5



mund consulting AG
Stuttgart, Germany
Remote
Senior
DevOps
Docker
Kubernetes

OPITZ CONSULTING
Berlin, Germany
Senior
Linux
DevOps
Ansible
Openshift
Terraform
+1

AllatNet Recruiting GmbH & Co. KG
GIT
Azure
Linux
DevOps
Docker
+8

Rocken AG
Zürich, Switzerland
Linux
DevOps
Openshift
Kubernetes
Elasticsearch
+1

Axians Amanox
Zürich, Switzerland
Go
ELK
Bash
Azure
DevOps
+14