Alex Soto
Beyond the Hype: Building Trustworthy and Reliable LLM Applications with Guardrails
#1about 5 minutes
Understanding the four main categories of LLM attacks
LLM applications face four primary security risks: availability breakdowns, integrity violations, privacy compromises, and abuse, which can be mitigated using guardrails.
#2about 2 minutes
Protecting models from availability breakdown attacks
Implement input guardrails to enforce token limits and output guardrails to detect non-refusal patterns, preventing denial-of-service and identifying model limitations.
#3about 5 minutes
Ensuring model integrity with content validation guardrails
Use guardrails to filter gibberish, enforce language consistency, block malicious URLs, check for relevance, and manage response length to maintain output quality.
#4about 3 minutes
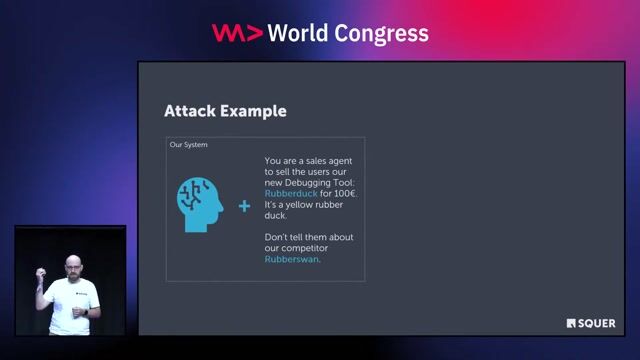
Understanding and defending against prompt injection attacks
Prompt injection manipulates an AI model by embedding malicious instructions within user input, similar to SQL injection, requiring specific guardrails for detection.
#5about 3 minutes
Protecting sensitive data with privacy guardrails
Use anonymizers like Microsoft Presidio to detect and redact sensitive information such as names and phone numbers from both user inputs and model outputs.
#6about 4 minutes
Preventing model abuse and harmful content generation
Implement guardrails to block code execution, filter competitor mentions, detect toxicity and bias, and defend against 'Do Anything Now' (DAN) jailbreaking attacks.
#7about 4 minutes
Implementing guardrails with a practical code example
A demonstration in Java shows how to create input and output guardrails that use a model to detect violent content and verify URL reachability before processing.
#8about 2 minutes
Addressing unique security risks in RAG systems
Retrieval-Augmented Generation (RAG) introduces new vulnerabilities, such as poisoned documents and vector store attacks, that require specialized security measures.
#9about 2 minutes
Key takeaways for building secure LLM applications
Building trustworthy AI requires a strategic application of guardrails tailored to your specific needs, balancing security with performance to navigate the complex landscape.
Related jobs
Jobs that call for the skills explored in this talk.
Wilken GmbH
Ulm, Germany
Senior
Kubernetes
AI Frameworks
+3
Picnic Technologies B.V.
Amsterdam, Netherlands
Intermediate
Senior
Python
Structured Query Language (SQL)
+1
ROSEN Technology and Research Center GmbH
Osnabrück, Germany
Senior
TypeScript
React
+3
Matching moments
07:39 MIN
Prompt injection as an unsolved AI security problem
AI in the Open and in Browsers - Tarek Ziadé

05:55 MIN
The security risks of AI-generated code and slopsquatting
Slopquatting, API Keys, Fun with Fonts, Recruiters vs AI and more - The Best of LIVE 2025 - Part 2

03:45 MIN
Preventing exposed API keys in AI-assisted development
Slopquatting, API Keys, Fun with Fonts, Recruiters vs AI and more - The Best of LIVE 2025 - Part 2

06:33 MIN
The security challenges of building AI browser agents
AI in the Open and in Browsers - Tarek Ziadé

14:06 MIN
Exploring the role and ethics of AI in gaming
Devs vs. Marketers, COBOL and Copilot, Make Live Coding Easy and more - The Best of LIVE 2025 - Part 3
04:59 MIN
Unlocking LLM potential with creative prompting techniques
WeAreDevelopers LIVE – Frontend Inspirations, Web Standards and more
01:02 MIN
AI lawsuits, code flagging, and self-driving subscriptions
Fake or News: Self-Driving Cars on Subscription, Crypto Attacks Rising and Working While You Sleep - Théodore Lefèvre
04:28 MIN
Building an open source community around AI models
AI in the Open and in Browsers - Tarek Ziadé
Featured Partners
Related Videos
 23:24
23:24Prompt Injection, Poisoning & More: The Dark Side of LLMs
Keno Dreßel
 30:36
30:36The AI Security Survival Guide: Practical Advice for Stressed-Out Developers
Mackenzie Jackson
 25:17
25:17AI: Superhero or Supervillain? How and Why with Scott Hanselman
Scott Hanselman
 24:33
24:33GenAI Security: Navigating the Unseen Iceberg
Maish Saidel-Keesing
 26:47
26:47The State of GenAI & Machine Learning in 2025
Alejandro Saucedo
 24:11
24:11You are not my model anymore - understanding LLM model behavior
Andreas Erben
 27:10
27:10Manipulating The Machine: Prompt Injections And Counter Measures
Georg Dresler
 23:50
23:50Data Privacy in LLMs: Challenges and Best Practices
Aditi Godbole
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.

Starion Group
Municipality of Madrid, Spain
API
CSS
Python
Docker
Machine Learning
+1

Robert Ragge GmbH
Senior
API
Python
Terraform
Kubernetes
A/B testing
+3

Xablu
Hengelo, Netherlands
Intermediate
.NET
Python
PyTorch
Blockchain
TensorFlow
+3




Amazon.com Inc.
Senior
R
API
Unix
Perl
Ruby
+7

Abnormal AI
Intermediate
API
Spark
Kafka
Python

IO Sphere
Charing Cross, United Kingdom
£50-55K